Articles tagged authorization
How to Build Secure Okta Node.js Integrations with DPoP

Integrating with Okta management API endpoints might be a good idea if you are trying to read or manage Okta resources programmatically. This blog demonstrates how to securely set up a node application to interact with Okta management API endpoints using a service app. Okta API management endpoints can be accessed using an access token issued by the Okta org authorization server with the appropriate scopes needed to make an API call. This can be...
Secure OAuth 2.0 Access Tokens with Proofs of Possession

In OAuth, a valid access token grants the caller access to resources and the ability to perform actions on the resources. This means the access token is powerful and dangerous if it falls into malicious hands. The traditional bearer token scheme means the token grants anyone who possesses it access. A new OAuth 2.0 extension specification, Demonstrating Proof of Possession (DPoP), defines a standard way that binds the access token to the OAuth client sending...
Elevate Access Token Security by Demonstrating Proof-of-Possession

We use access tokens to request data and perform actions within our software systems. The client application sends a bearer token to the resource server. The resource server checks the validity of the access token before acting upon the HTTP request. What happens if the requesting party is malicious, steals your token, and makes a fraudulent API call? Would the resource server honor the HTTP request? If you use a bearer token, the answer is...
The Things to Keep in Mind about Auth
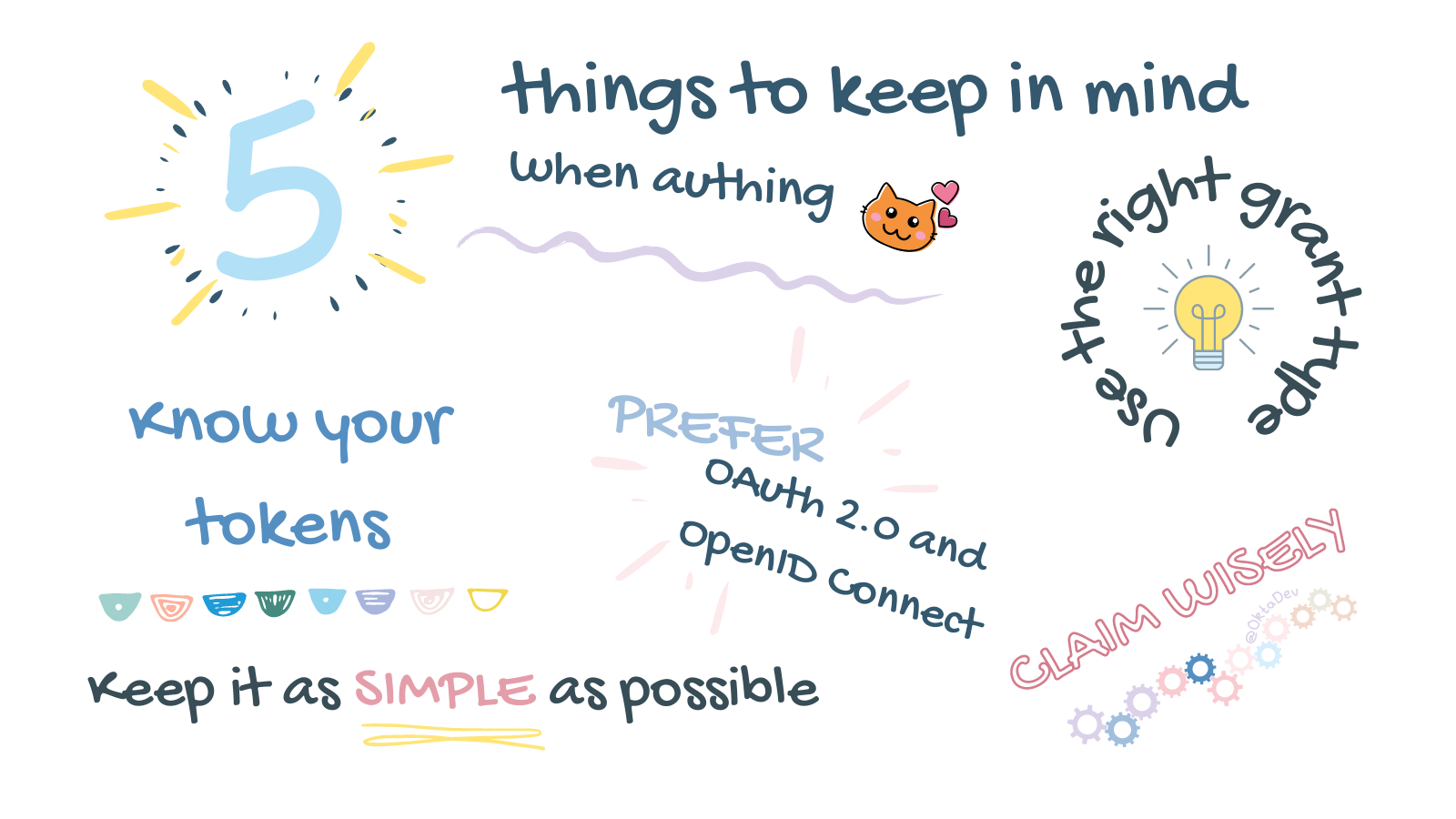
There’s a lot of information out there about adding authentication to your app, which is helpful! But also overwhelming. It can be hard to find relevant and up-to-date information. Security best practices and technologies change, so refreshing your understanding and keeping up with current best practices is a good thing. Here are some notes I took while I reviewed my knowledge and applied my experience implementing auth. Prefer OAuth 2.0 and OpenID Connect If you’re...
Developer Day 2021: Celebrating the Future of Identity

It’s been a big year for Okta and Auth0. Our two companies have officially joined forces over the past few months, and we are excited about the chance to shape the future of identity together. It’s great to celebrate our combined developer communities at the first Developer Day event. I look forward to exploring more ways we can collaborate with our Auth0 counterparts and far-flung global communities through future events and activities. On Tuesday, 8/24,...
Use Okta and Oso to Secure a FastAPI + SQLAlchemy App

FastAPI is really fast and SQLAlchemy is really…SQL-y. But what good is a fast and SQL-y application if it isn’t secure? In this post, we’re going to show you how to secure a fast and SQL-y app! First we will need some authentication, which is how we identify who the user is. We’ll use Okta for this. Next, we’ll want to perform authorization, which controls what the user can do in our application. We’ll be...
An Illustrated Guide to OAuth and OpenID Connect
In the “stone age” days of the Internet, sharing information between services was easy. You simply gave your username and password for one service to another so they could login to your account and grab whatever information they wanted! Yikes! You should never be required to share your username and password, your credentials, to another service. There’s no guarantee that an organization will keep your credentials safe, or guarantee their service won’t access more of...
PHP Authorization with OAuth 2.0 and Okta

User account management, authorization, and access control can be difficult to implement for many web developers. At the same time, they are critical cornerstones of application security – any mistake can lead to data leaks, financial losses, and legal troubles. Successful web applications inevitably grow to a stage where simple user authorization is no longer sufficient and certain features have to be made available only to certain users. There are a variety of ways to...
Implement the OAuth 2.0 Authorization Code with PKCE Flow

Imagine two levers that are inversely connected. That is, as one goes up, the other goes down. One lever is User Experience and the other is Security. It’s not a perfect analogy, but most developers can attest that as user experience goes up, security goes down. Take browser history syncing for example. I can start a session with my bank on Firefox mobile and pick up right where I left off on Firefox desktop. From...
Decode JWTs in C# for Authorization

There are two main steps in securing an application: authentication and authorization. Authentication is easy enough. A user enters a username and password (maybe even a second factor) to prove (authenticate) who they are. Authorization is a little less cut and dried. There are lots of factors that go into what an authenticated user is authorized to do. First, you need some information about the user that just authenticated. Many modern web apps use JSON...
Add Login to Your ASP.NET Core MVC App

One of the improvements in the latest version of ASP.NET Core (MVC ) is a new and simplified authentication integration. However, managing authentication on your own is still a considerable burden. Not only do you need to handle signup and login, but you also have to set up the database, manage security aspects of registration and login, and take care of session management. Since the integration of external auth providers has never been more comfortable,...
Policy-Based Authorization in ASP.NET Core
The authorization model in ASP.NET Core got a significant overhaul with the introduction of policy-based authorization. Authorization now uses requirements and handlers, which are decoupled from your controllers and loosely coupled to your data models. The result is a more modular, more testable authorization framework that fits into the modern ASP.NET Core approach nicely. If you’ve built a web or mobile app before, you know that even without these changes to ASP.NET Core’s authorization model,...
User Authorization in ASP.NET Core with Okta
Authorization is the oft-forgotten piece of identity and access management. The fact is, almost every app needs more than just “are they signed in?” for authorization. Most times, you need to not only know who “they” are, but what access they are supposed to have. For instance, “are they in the administrator group?” or “are they in a group with some special privileges?” Today, you’ll learn how to do this with Okta in an ASP.NET...
Meet the New Okta Identity Platform
I’m genuinely excited to announce that today, we’re officially re-launching the new and improved Okta Identity Platform. Everything has been molded to our vision, and we’re aiming to do something we could not before: build the world’s largest authentication-as-a-service platform for developers of all shapes and sizes. The new Okta Identity Platform is our attempt to make authentication and authorization problems a relic of the past. We want to provide beautiful developer libraries across every...
What the Heck is OAuth?
There’s a lot of confusion around what OAuth actually is. Some people think OAuth is a login flow (like when you sign into an application with Google Login), and some people think of OAuth as a “security thing”, and don’t really know much more than that. I’m going to show you what OAuth is, explain how it works, and hopefully leave you with a sense of how and where OAuth can benefit your application. What...