Articles tagged cryptography
Five Anti-Patterns with Secrets in Java

Most applications require some sort of secret or password to enable access: database connection info, API keys, OAuth client secrets, and JWT keys, to list some examples. Dealing with secrets in your projects is always a chore, and it’s often done wrong. In this post, I’ll describe five common problems, which you can think of as anti-patterns (the opposite of a best practice) and I’ll offer suggestions to help you avoid these issues. Table of...
A Thorough Introduction to PASETO
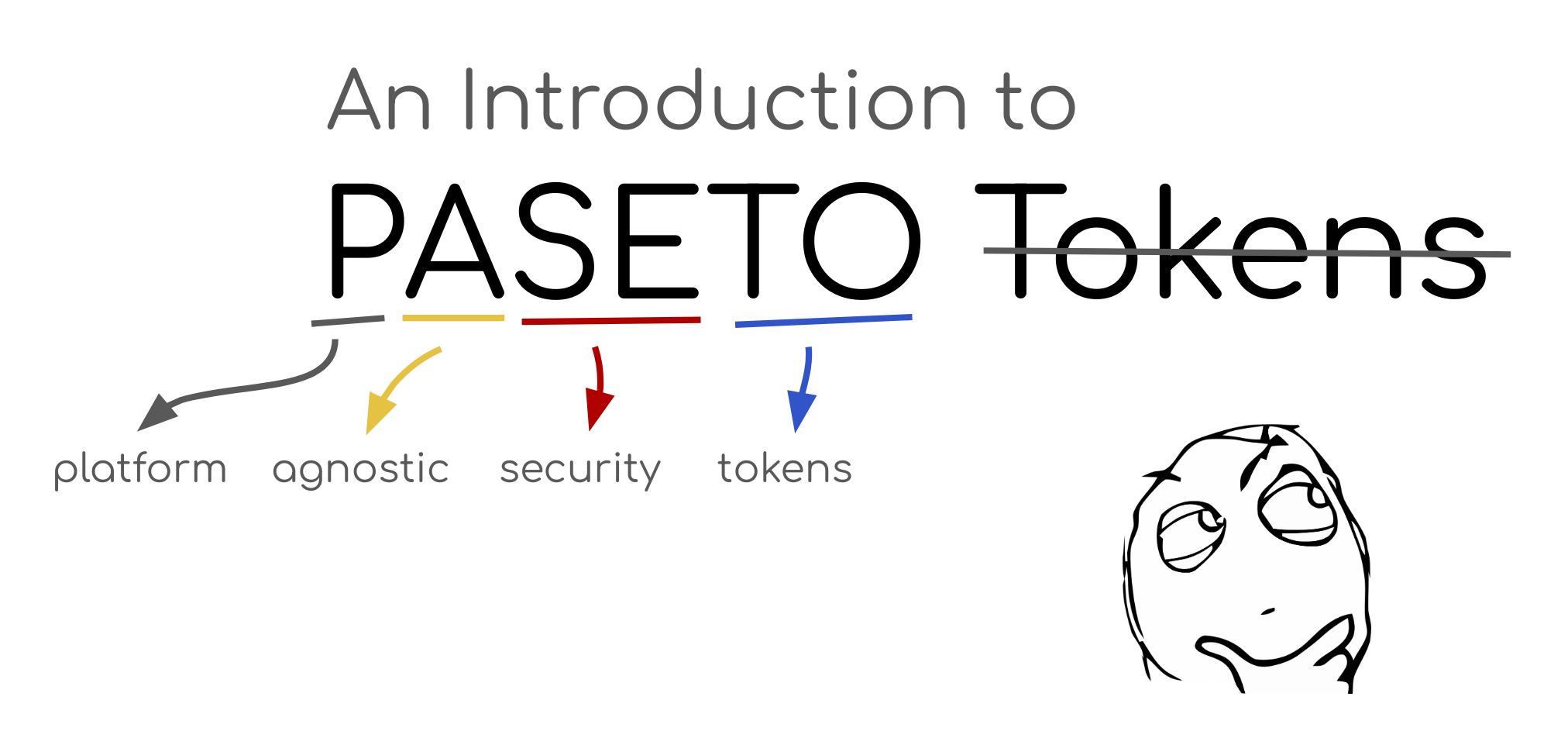
Today I’m going to introduce you to one of my favorite pieces of security technology released in the last several years: PASETO (platform-agnostic security tokens). PASETO is a relatively new protocol, designed by Scott Arciszewski in early 2018 that is quickly gaining adoption in the security community. While PASETO is still a young technology, I thought it’d be interesting to take an in-depth look at it, since it’s both incredibly useful and solves a lot...
Why Public Key Cryptography Matters
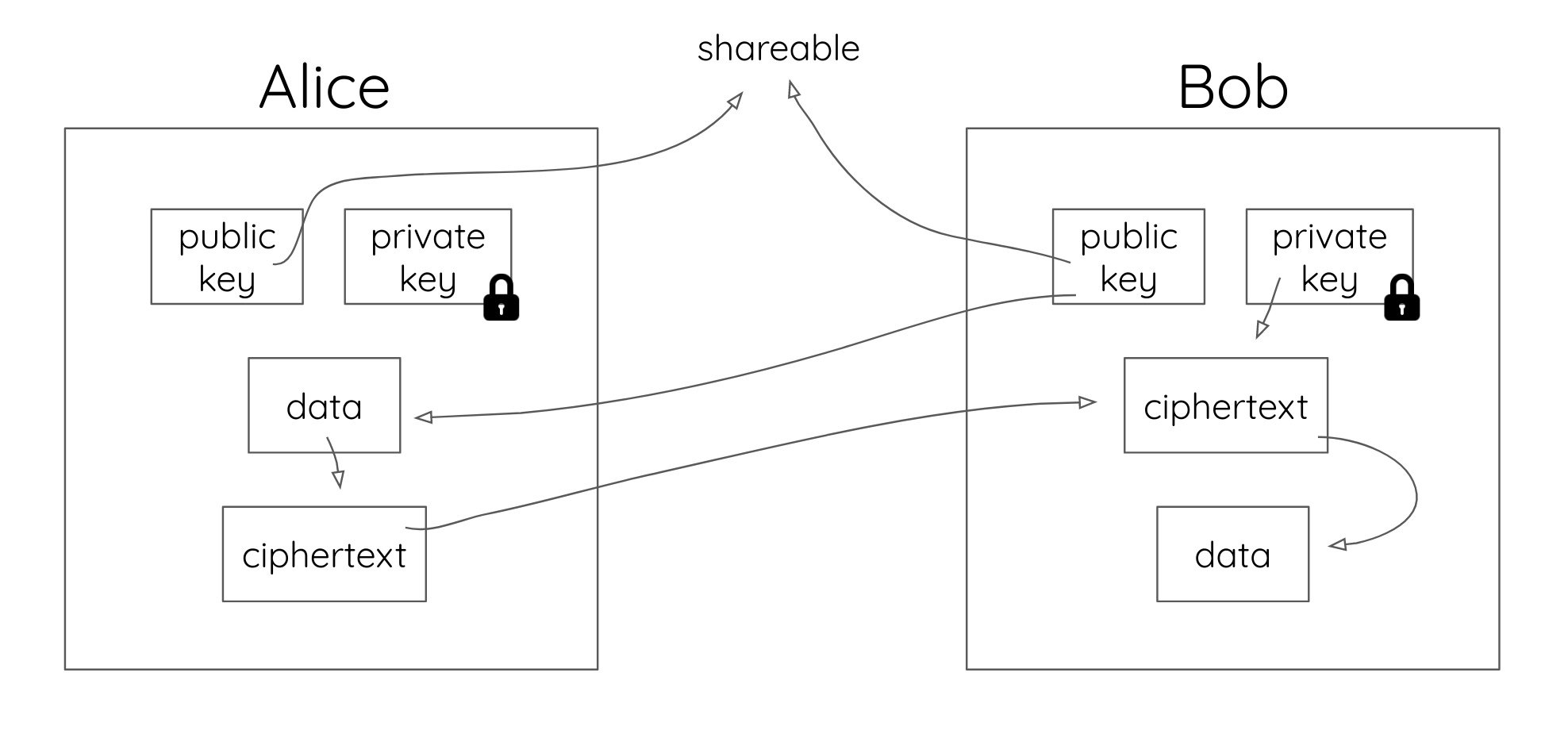
40 years old and as relevant today as when it was first invented, public key cryptography is the unsung hero of modern cybersecurity. Most people take unknowing advantage of it many times a day. So what is it, and how does it work? Let’s start by reviewing the concept of symmetric encryption, which allows you to encrypt information using a shared secret key. It’s not a modern idea—even Julius Caesar used it to code his...
The Hardest Thing About Data Encryption
Encrypting data is all about making sure that only the right people can view the data you’ve encrypted. There are two primary forms of data encryption: symmetric and asymmetric. While you can easily Google “symmetric encryption best practices” and figure out the best algorithms and developer libraries to use (more on this later) to encrypt and decrypt data, one thing isn’t so easy: figuring out how to properly store and manage your data encryption keys....