Implement Introspection Flow With Kong Konnect and Okta

In our third Kong and Okta tutorial, we’ll go through the introspection flow implementation. This series will show you how to implement service authentication and authorization for Kong Konnect and Okta using the OpenID Connect (OIDC) plugin. Parts 1, 2 and 4 cover:
- Implement Client Credentials with Kong Konnect and Okta
- Authorization Code for user authentication
- Access control based on Okta’s groups and planes
Table of Contents
- Konnect and Okta Integration Topology
- Set Up the Okta Application
- Apply the OpenID Connect Plugin
- Test the Introspection Flow With Insomnia
- Deactivate the Okta Application
- Protect Your Applications with Kong Konnect and Okta
You can also watch this tutorial as a screencast.
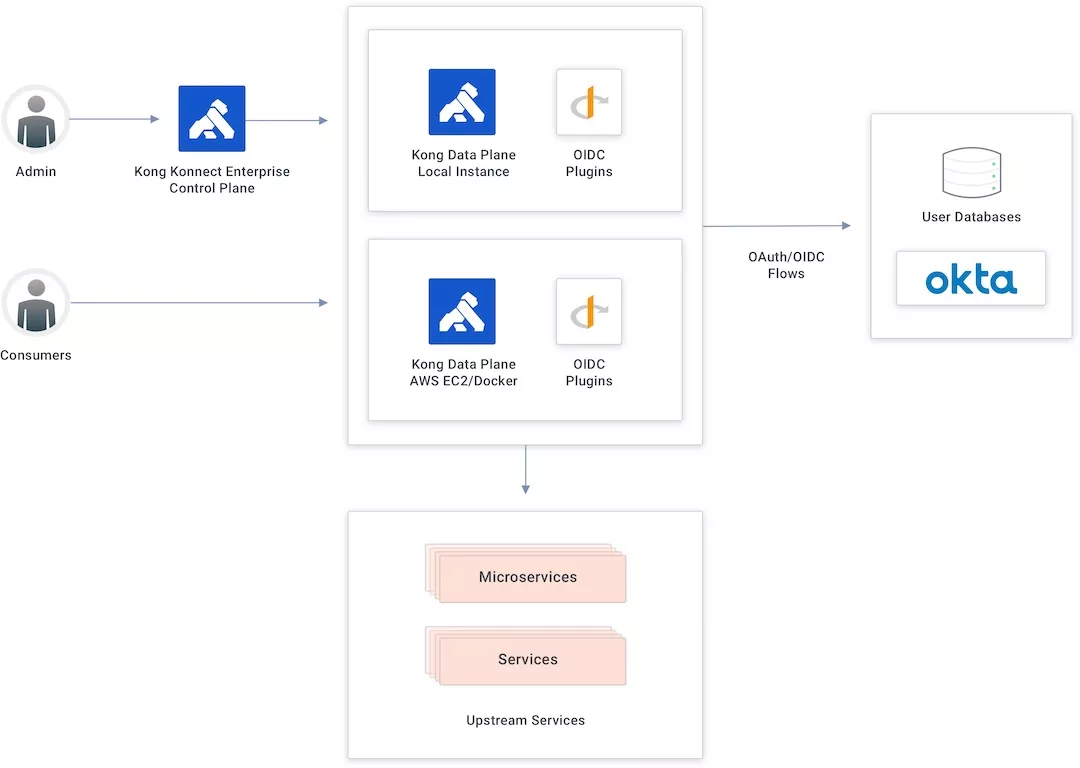
Konnect and Okta Integration Topology
In this example, I’m using the Konnect control plane to create new APIs and policies and publish them to my data plane running as a Docker container in an AWS EC2 instance.
Introspection Flow
The introspection flow is part of the token validation process. Kong Gateway evaluates the injected token at the request processing time to see if it’s still valid to the upstream services. The evaluation hits a specific Okta endpoint, passing the received token. Based on the response provided by Okta, Kong Gateway accepts or rejects the request.
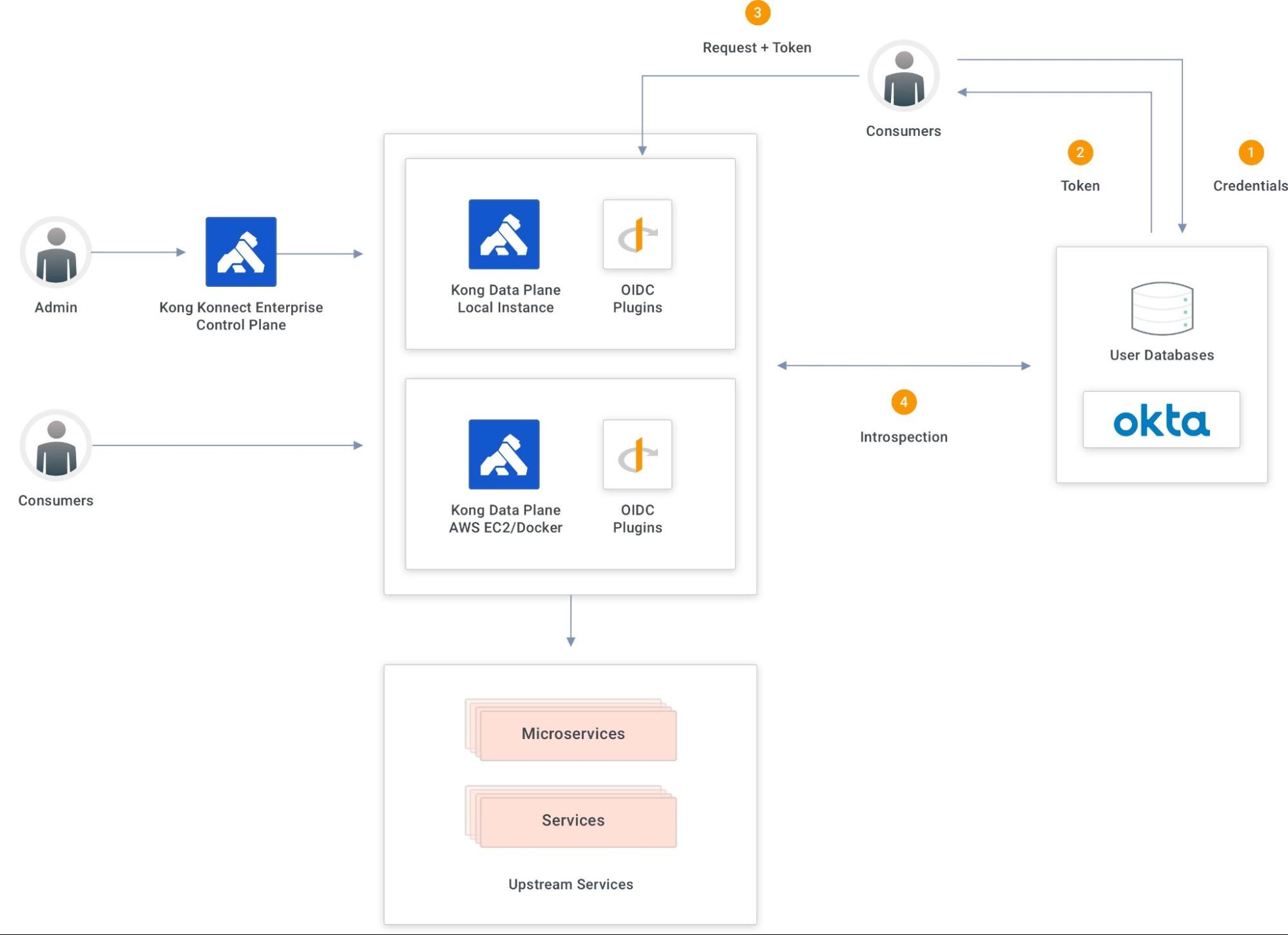
For production environments, the OIDC plugin provides caching capabilities for the Okta responses. However, for this tutorial, I’m going to disable caching to better view the flow.
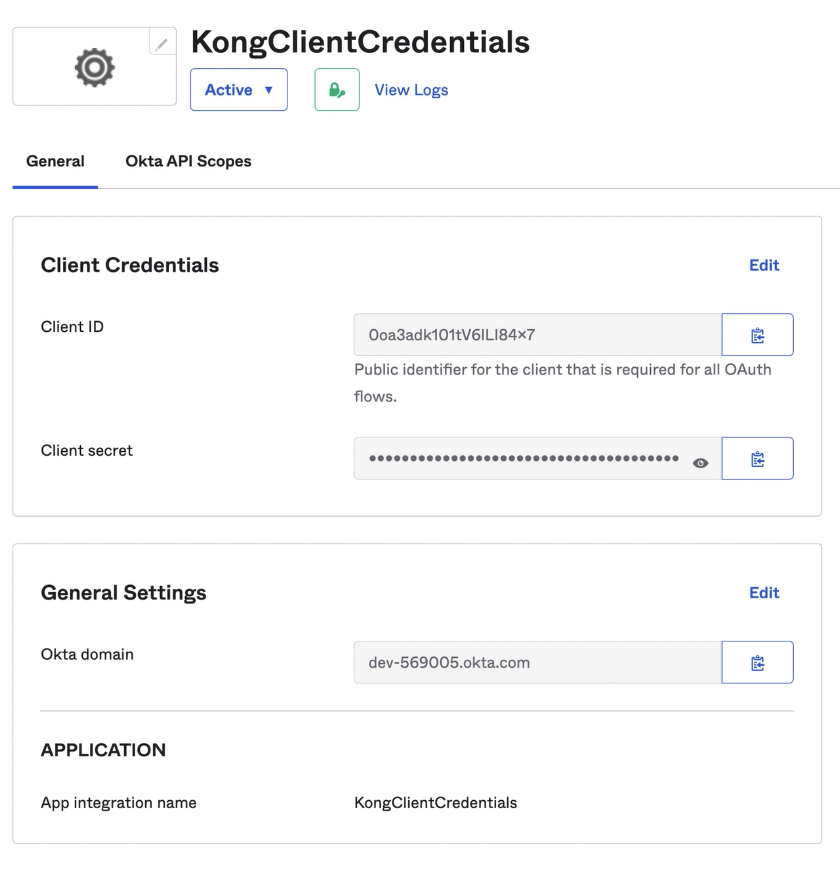
Set Up the Okta Application
Regarding Okta’s settings, I’m going to use the same client credentials application I created before. With the client ID and client secret. However, my OIDC plugin has to be set with specific parameters to implement introspection.
Apply the OpenID Connect Plugin
In the Konnect ServiceHub, I have an IntrospectionRoute OIDC plugin enabled.
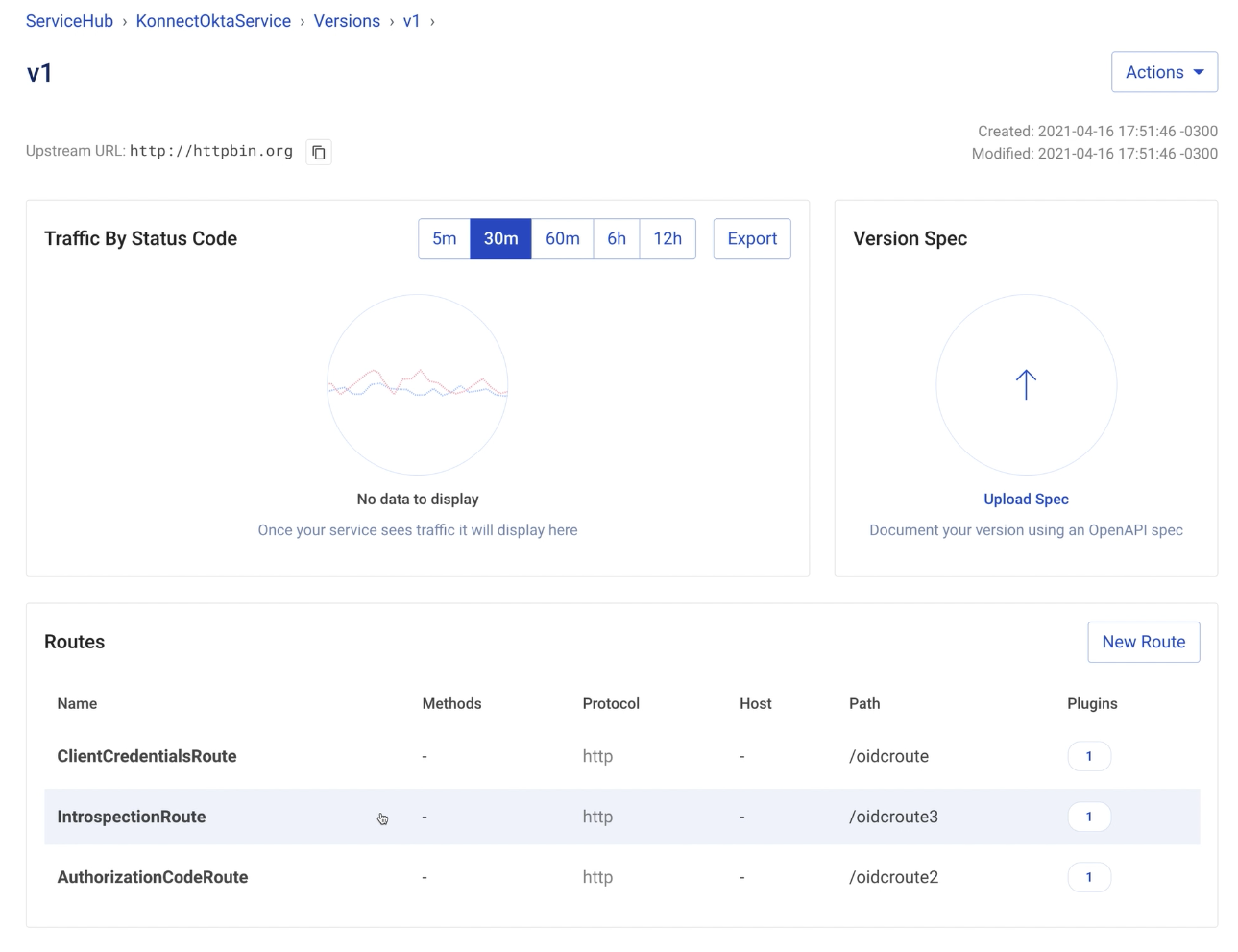
The settings should be:
-
Config.Auth Methods

-
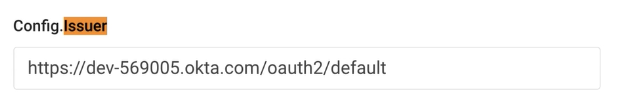
Config.Issuer
-
Config.Introspect Jwt Tokens

-
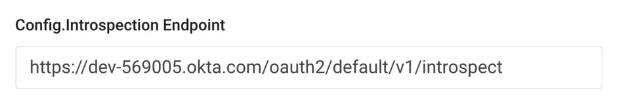
Config.Introspection Endpoint with a specific endpoint provided by Okta to implement introspection
Test the Introspection Flow With Insomnia
To better view the flow, I will use Insomnia, Kong’s API spec editor, to send requests to both Okta and Konnect. Below are my two requests.
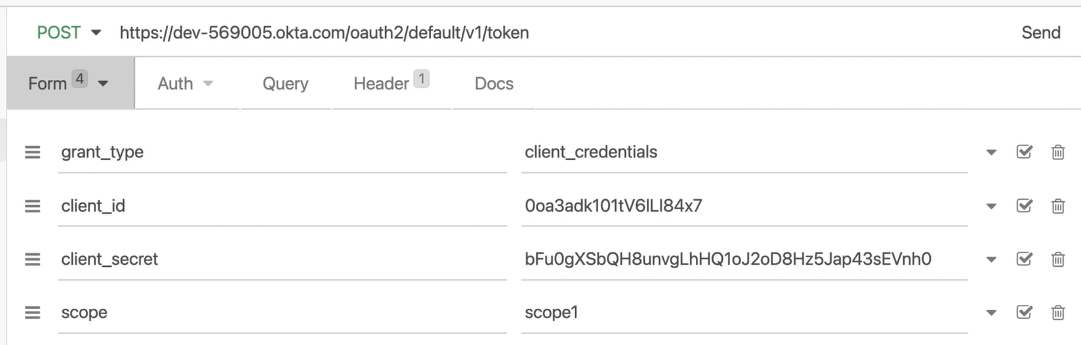
The first one I’m sending to Okta, passing the expected parameters to get it authenticated and receive a token.
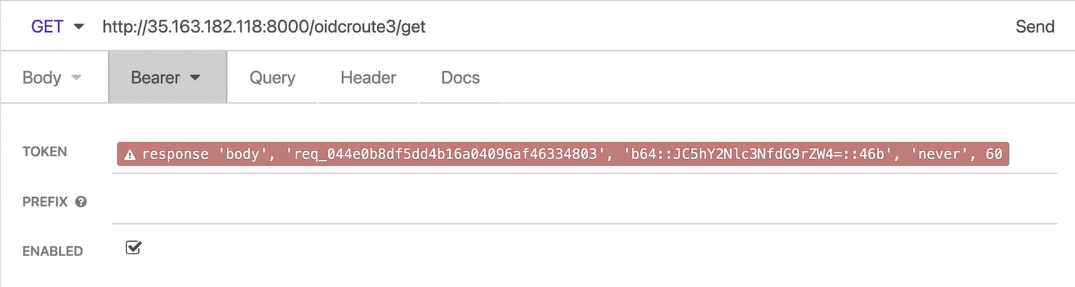
For the second one to consume the route, I’m using a specific Insomnia capability called Request Chaining. With this, I’ll be able to extract values from the response of a given request to build new ones. In my case, I’m pulling the access token from Okta’s response to make the other request and then send it to Konnect.
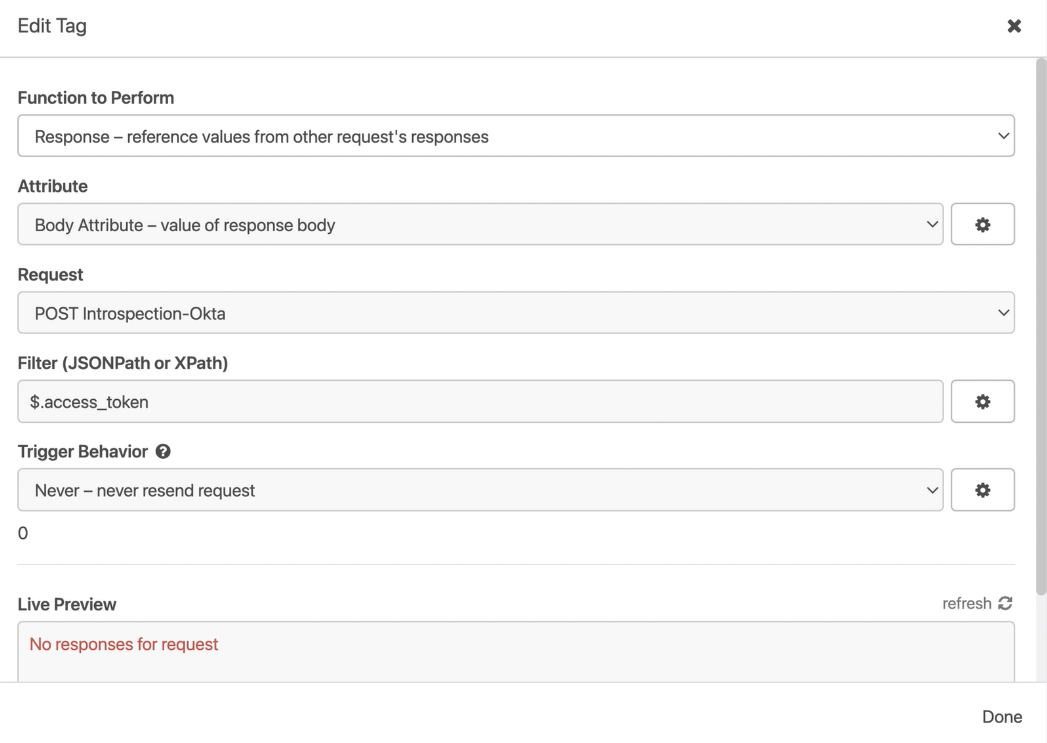
Next, let’s send a request to Okta to get our token. There it is.
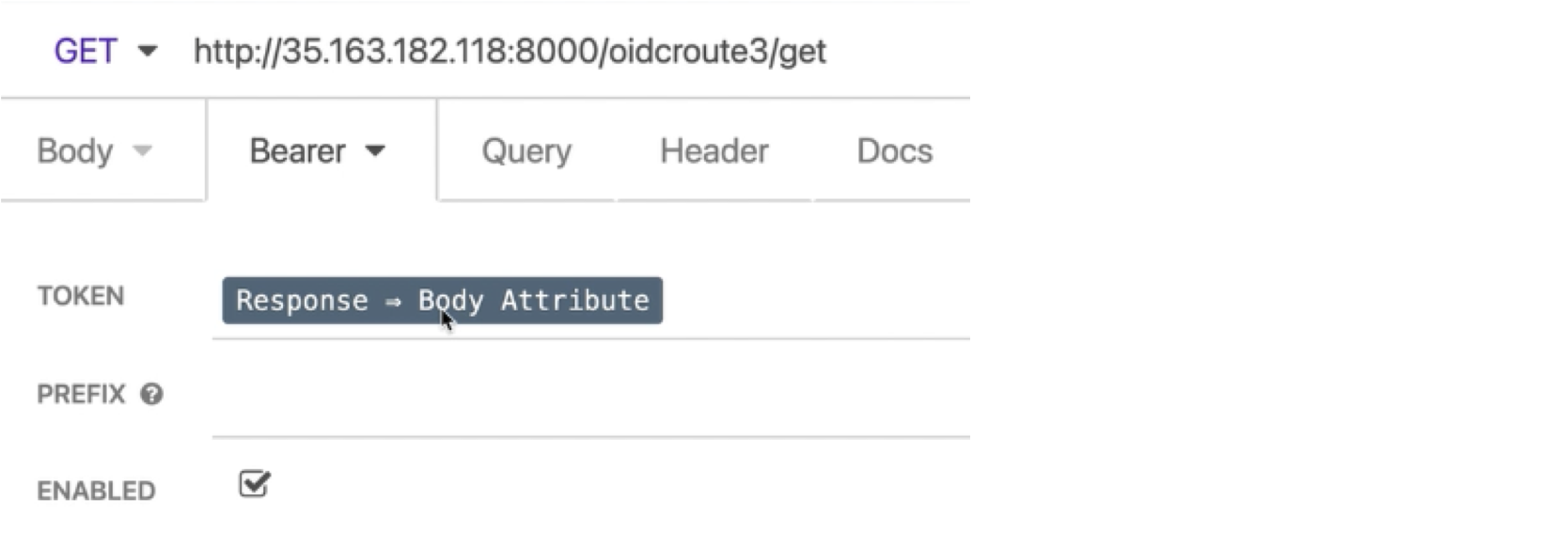
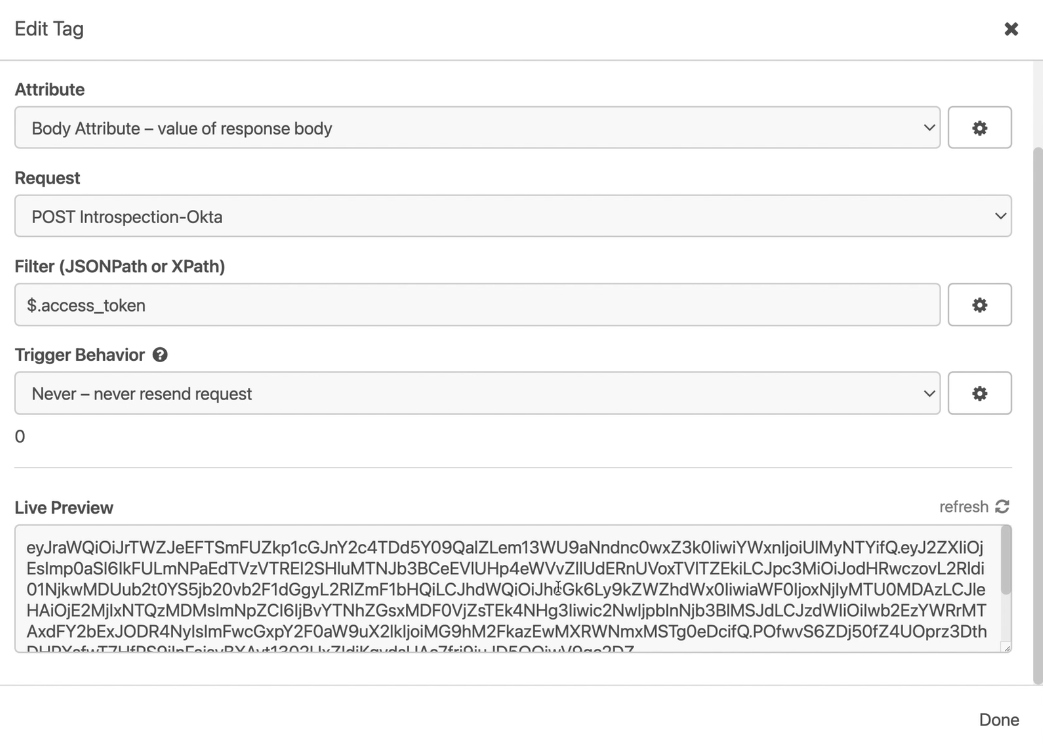
This time, we can see that Kong’s request is ready to be sent since we got Okta’s token injected inside of it.
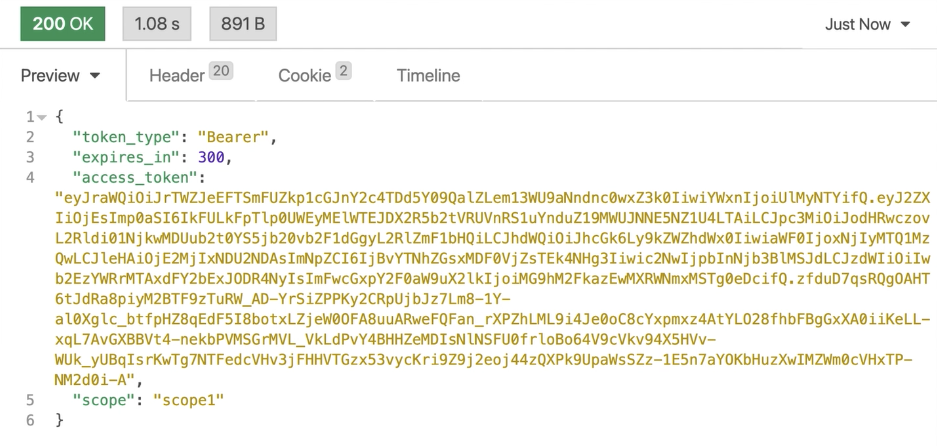
And here’s the Konnect response:
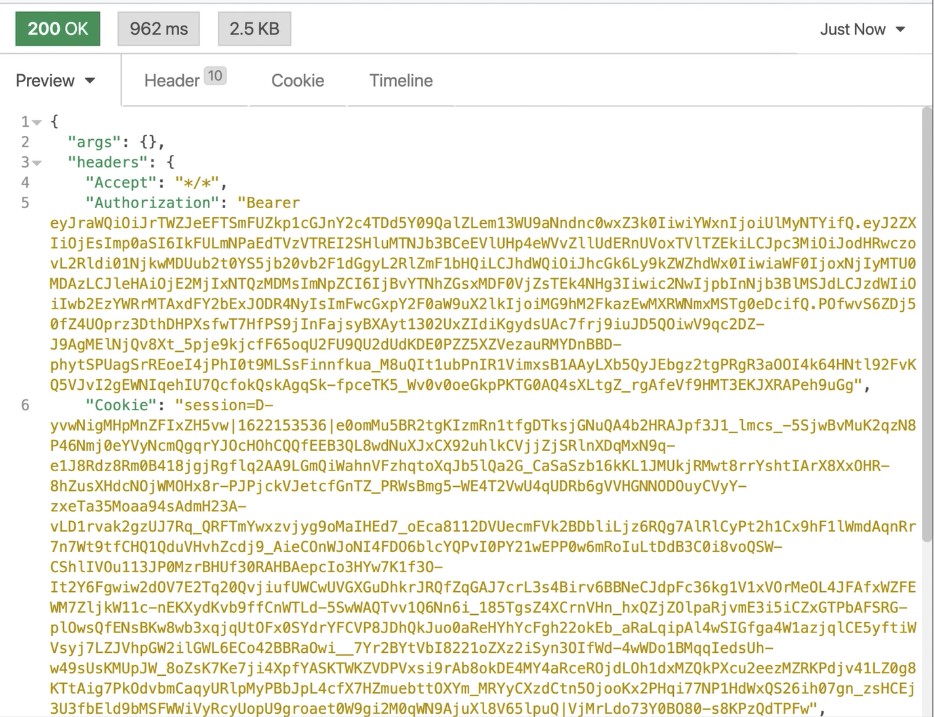
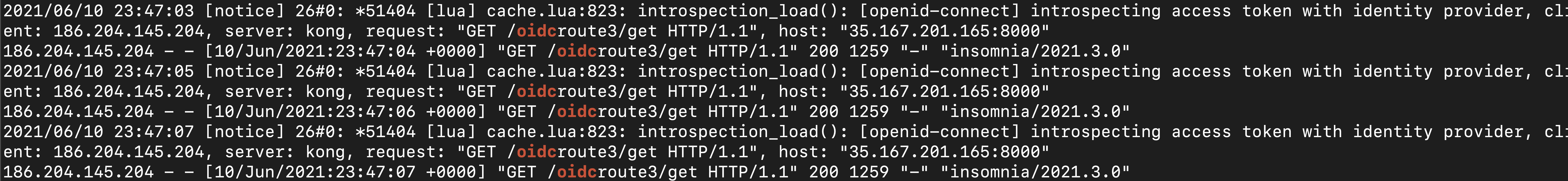
It’s important to note that Konnect is validating the token behind the scenes. Here’s one EC2 terminal where my data plane is running. Since I disabled introspection caching for the OIDC plugin, Konnect hits Okta for each request to validate the token.
Deactivate the Okta Application
Another way to see introspection is by deactivating the Okta application. All tokens related to it will be considered invalid and, as a consequence, will not be accepted by Kong again.
Let’s get back to Okta’s application and deactivate it. We should get a 401 error code from Kong.
Protect Your Applications with Kong Konnect and Okta
Start a free trial, or contact Kong if you have any questions as you’re getting set up.
Once you’ve set up Konnect and Okta introspection flow, you may find these other tutorials helpful:
- Automating Your Developer Pipeline With APIOps (DevOps + GitOps)
- Service Design Guidelines Part 2: API Versioning
- “Gateway Mode” in Kuma and Kong Mesh
- Use Kong Gateway to Centralize Authentication
If you have any questions about this post, please leave a comment below. To be notified when the OktaDev team posts new content, please follow @oktadev on Twitter, like them on LinkedIn, or subscribe to their YouTube channel.
Okta Developer Blog Comment Policy
We welcome relevant and respectful comments. Off-topic comments may be removed.